Question 1
Refer to the exhibit. What does the (*) represent in the output?| 02:16:29: NAT: s=10.10.0.2->1.2.4.2, d=1.2.4.1 [51607] 02:16:29: NAT: s=1.2.4.1, d=1.2.4.2->10.10.0.2 [55227] 62:16:29: NAT*: s=10.10.0.2->1.2.4.2, d=1.2.4.1 [51608] 02:16:29: NAT*: s=10.10.0.2->1.2.4.2, d=1.2.4.1 [51609] |
B. Packet was translated, but no response was received from the distant device.
C. Packet was not translated, because no additional ports are available.
D. Packet was translated and fast switched to the destination.
Answer: D
Explanation
The above output is from the “debug ip nat” command. In this output, the first two lines show the Domain Name System (DNS) request and reply debugging output.In the first line (DNS request):
s=10.10.0.2->1.2.4.2: source of the IP address (10.10.0.2) and how it is being translated (to 1.2.4.2)
d=1.2.4.1: destination address of the packet
[51607]: the IP identification number of the packet
In the second line (DNS reply):
s=1.2.4.1: source of the reply
d=1.2.4.2->10.10.0.2: how the destination is being translated
The remaining lines show debugging output from a Telnet connection from a host on the inside of the network to a host on the outside of the network. All Telnet packets, except for the first packet, were translated in the fast path, as indicated by the asterisk (*).
Note: If the connection is already established, the security appliance does not need to re-check packets and the packets are sent to the Fast Path.
Question 2
Refer to the exhibit. What command sequence will enable PAT from the inside to outside network?| ip nat pool isp-net 1.2.4.10 1.2.4.240 netmask 255.255.255.0 ! interface ethernet 1 description ISP Connection ip address 1.2.4.2 255.255.255.0 ip nat outside ! interface ethernet 0 description Ethernet to Firewall eth0 ip address 10.10.0.1 255.255.255.0 ip nat inside ! access-list 1 permit 10.0.0.0 0.255.255.255 |
B. (config-if)# ip nat outside overload
C. (config)# ip nat inside source list 1 interface ethernet1 overload
D. (config-if)# ip nat inside overload
Answer: C
Explanation
The command “ip nat inside source list 1 interface ethernet1 overload” means:“ip nat”: use NAT
“inside”: NAT from inside to outside
“source list 1″: the source addresses can be found in access list 1
“interface ethernet1″: NAT out of this interface
“overload”: use NAT overload (PAT)
Question 3
Refer to the exhibit. A junior network engineer has prepared the exhibited configuration file. What two statements are true of the planned configuration for interface fa0/1? (Choose two)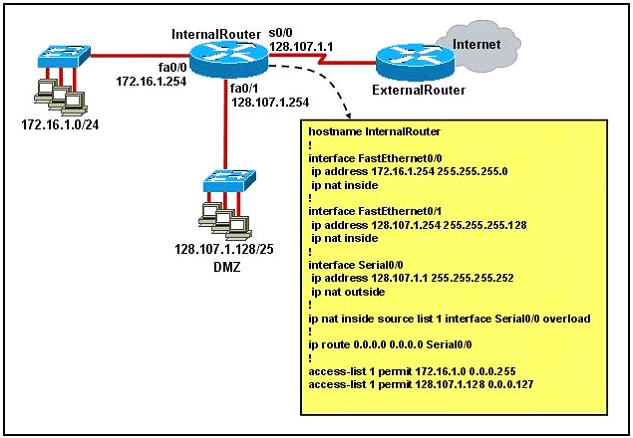
A. The two FastEthernet interfaces will require NAT configured on two outside serial interfaces.
B. Address translation on fa0/1 is not required for DMZ Devices to access the Internet.
C. The fa0/1 IP address overlaps with the space used by s0/0.
D. The fa0/1 IP address is invalid for the IP subnet on which it resides.
E. Internet hosts may not initiate connections to DMZ Devices through the configuration that is shown.
Answer: B E
Explanation
Both inside FastEthernet interfaces can use only one outside interface to go to the Internet -> A is not correct.DMZ devices use IP addresses in the range of 128.107.1.128/25 which are public IP addresses so they don’t need address translation to access the Internet -> B is correct.
The fa0/1 interface’s IP address is 128.107.1.254 255.255.255.128 (range from 128.107.1.128 to 128.107.1.255) while the IP address of s0/0 is 128.107.1.1 255.255.255.252 (ranges from 128.107.1.0 to 128.107.1.4) so they are not overlapped with each other -> C is not correct.
DMZ devices are in the range of 128.107.1.128/25 (from 128.107.1.128 to 128.107.1.255) and fa0/1 IP address (128.107.1.254) is a valid IP address on this subnet -> D is not correct.
DMZ devices (and other internal hosts) are using dynamic PAT, which is a type of dynamic NAT. With dynamic NAT, translations do not exist in the NAT table until the router receives traffic that requires translation. In other words, if DMZ devices communicate with outside hosts first, dynamic translation works fine. But if outside hosts communicate with DMZ devices first, no translation is created in NAT table and the packets will be dropped. This is the reason why “Internet hosts may not initiate connections to DMZ Devices through the configuration that is shown” -> E is correct.
Question 4
Refer to the exhibit. What statement is true of the configuration for this network?
A. The configuration that is shown provides inadequate outside address space for translation of the number of inside addresses that are supported.
B. Because of the addressing on interface FastEthernet0/1, the Serial0/0 interface address will not support the NAT configuration as shown.
C. The number 1 referred to in the ip nat inside source command references access-list number 1.
D. ExternalRouter must be configured with static routers to network 172.16.2.0/24
Answer: C
Explanation
The “list 1″ refers to the access-list number 1.Question 5
What are two benefits of using NAT? (choose two)A. NAT protects network security because private networks are not advertised.
B. NAT accelerates the routing process because no modifications are made on the packets.
C. Dynamic NAT facilitates connections from the outside of the network.
D. NAT facilitates end-to-end communication when IPsec is enable.
E. NAT eliminates the need to re-address all host that require external access.
F. NAT conserves addresses through host MAC-level multiplexing.
Answer: A E
Explanation
By not reveal the internal Ip addresses, NAT adds some security to the inside network -> A is correct.NAT has to modify the source IP addresses in the packets -> B is not correct.
Connection from the outside of the network through a “NAT” network is more difficult than a more network because IP addresses of inside hosts are hidden -> C is not correct.
In order for IPsec to work with NAT we need to allow additional protocols, including Internet Key Exchange (IKE), Encapsulating Security Payload (ESP) and Authentication Header (AH) -> more complex -> D is not correct.
By allocating specific public IP addresses to inside hosts, NAT eliminates the need to re-address the inside hosts -> E is correct.
NAT does conserve addresses but not through host MAC-level multiplexing. It conserves addresses by allowing many private IP addresses to use the same public IP address to go to the Internet -> F is not correct.
Question 6
Which two statements about static NAT translations are true? (choose two)A. They are always present in the NAT table.
B. They allow connection to be initiated from the outside.
C. They can be configured with access lists, to allow two or more connections to be initiated from the outside.
D. They require no inside or outside interface markings because addresses are statically defined.
Answer: A B
Explanation
With static NAT, translations exist in the NAT translation table as soon as you configure static NAT command(s), and they remain in the translation table until you delete the static NAT command(s).With dynamic NAT, translations do not exist in the NAT table until the router receives traffic that requires translation. Dynamic translations have a timeout period after which they are purged from the translation table.
-> A is correct.
Because static NAT translations are always present in the NAT table so outside hosts can initiate the connection without being dropped -> B is correct.
Static translations can not be configured with access lists. To configure static NAT, we only need to specify source IP, NAT IP, inside interface & outside interface.
-> C is not correct.
We have to specify which is the inside and outside interface -> D is not correct.
For your information, below is an example of configuring static NAT:
R0(config)#int f0/0
R0(config-if)#ip nat inside
R0(config-if)#int f0/1
R0(config-if)#ip nat outside
R0(config)#ip nat inside source static 10.0.0.1 200.0.0.2
Question 7
Refer to the exhibit. Which statement about packet addresses are true during data exchange when host A makes Web-request to WWW Server, considering that there is NAT overload scheme for data passing from Corp LAN hosts to outside networks in use?
B. Source 200.15.239.128:3015 and destination 192.168.10.34:80
C. Destination 192.168.10.11:3015 and source 200.15.239.128:80
D. Source 192.168.10.34:80 and destination 192.168.10.254:3015
E. Destination 234.15.27.225:3015 and source 200.15.239.128:80
Answer: E
Explanation
From A to Corp router: + Source: 192.168.10.34: 3015 & Destination: 200.15.239.128:80
From Corp to WWW Server:
+ Source: 234.15.27.225:3015 & Destination: 200.15.239.128:80
From WWW Server to Corp:
+ Source: 200.15.239.128:80 & Destination: 234.15.27.225:3015
From Corp to Host A:
+ Source: 192.168.10.254:80 & Destination: 192.168.10.34:3015
So the only correct answer is E (from WWW server to Corp)
No comments:
Post a Comment