Question 1
Which statement about RIPng is true?
A. RIPng allows for routes with up to 30 hops.
B. RIPng is enabled on each interface separately.
C. RIPng uses broadcasts to exchange routes.
D. There can be only one RIPng process per router.
Answer: B
Explanation
RIPng is similar to RIPv2 but is used for IPv6. But unlike RIPv1 and RIPv2, RIPng is enabled on each interface separately. For example:
Router(config)#ipv6 unicast-routing (Enables the forwarding of IPv6 unicast datagrams globally on the router)
Router(config)#interface fa0/0
Router(config-if)#ipv6 rip 9tut enable (9tut is the process name of this RIPng)
Question 2
What are two characteristics of RIPv2? (Choose two)
A. classful routing protocol
B. variable-length subnet masks
C. broadcast addressing
D. manual route summarization
E. uses SPF algorithm to compute path
Answer: B D
Question 3
Refer to the exhibit. Which (config-router) command will allow the network represented on the interface to be advertised by RIP?
router rip
version 2
no auto summary
!
interface ethernet0
ip address 10.12.6.1 255.255.0.0 |
A. redistribute ethernet0
B. network ethernet0
C. redistribute 10.12.0.0
D. network 10.12.0.0
Answer: D
Question 4
Refer to the exhibit. What information can be gathered from the output?
RouterA#debug ip rip
RIP protocol debugging is on00:34:32: RIP: sending v2 flash update to 224.0.0.9 via FastEthernet8/0 (172.16.1.1)
00:34:32: RIP: build flash update entries
00:34:32: 10.10.1.0/24 via 0.0.0.6, metric 1, tag 0
00:34:32: RIP: sending v2 flash update to 224.0.0.9 via Loopback (10.10.1.1)
00:34:32: RIP: build flash update entries
00:34:32: 10.0.0.0/8 via 0.6.0.0, metric 2, tag 0
00:34:32: 172.16.1.0/24 via 0.0.0.0, metric 1, tag 0
00:34:32: RIP: ignored v2 packet from 16.10.1.1 (sourced from one of our addresses)
06:34:33: RIP: received v2 update from 172.16.1.2 on FastEthernet0/6
66:34:33: 16.6.0.0/8 via 6.0.6.6 in 1 hops
66:34:44: RIP: sending v2 update to 224.6.6.9 via FastEthernet0/0 (172.16.1.1)
66:34:44: RIP: build update entries
66:34:44: 10.10.1.0/24 via 0.0.0.0, metric 1, tag 0 |
A. One router is running RIPv1.
B. RIP neighbor is 224.0.0.9.
C. The network contains a loop.
D. Network 10.10.1.0 is reachable.
Answer: D
Question 5
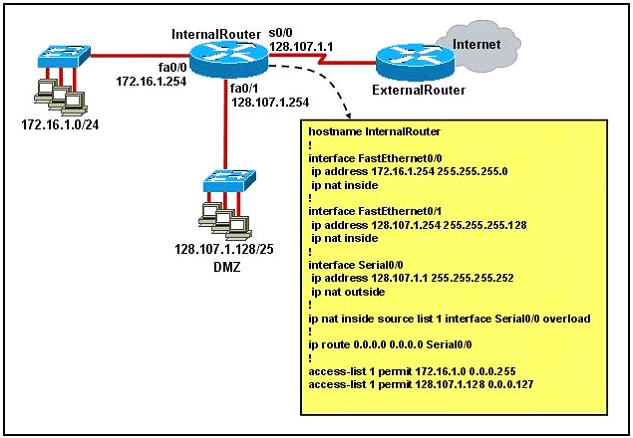
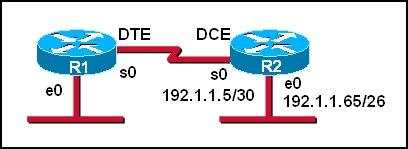
Which series of commands will configure router R1 for LAN-to-LAN communication with router R2? The enterprise network address is 192.1.1.0/24 and the routing protocol in use is RIP. (Choose three)
A.
R1 (config)# interface ethernet 0
R1 (config-if)# ip address 192.1.1.129 255.255.255.192
R1 (config-if)# no shutdown
B.
R1 (config)# interface ethernet 0
R1(config-if)#ip address 192.1.1.97 255.255.255.192
R1 (config-if)# no shutdown
C.
R1 (config)# interface serial 0
R1 (config-if)# ip address 192.1.1.4 255.255.255.252
R1 (config-if)# clock rate 56000
D.
R1 (config)# interface serial 0
R1(config-if)#ip address 192.1.1.6 255.255.255.252
R1 (config-it)# no shutdown
E.
R1 (config)# router rip
R1 (config-router)# network 192.1.1.4
R1 (config-router)# network 192.1.1.128
F.
R1 (config)# router rip
R1 (config-router)# version 2
R1 (config-router)# network 192.1.1.0
Answer: A D F
Explanation
First we notice that the ip address of the E0 interface of R2 is 192.1.1.65/26, which has:
+ Increment: 64 (/26 = 1111 1111.1111 1111.1111 1111.1
100 0000)
+ Network address:
192.1.1.64
+ Broadcast address:
192.1.1.127
Therefore, the ip address of the E0 interface of R1 cannot belong to this range or the network cannot operate correctly.
In answer A, the ip address of E0 interface of R1 is 192.1.1.129, which does not belong in this range -> A is correct.
In answer B, E0 interface of R1 has the ip address of 192.1.1.97, which belongs in this range -> B is not correct.
The s0 interface of R1 must belong to the same network of s0 interface of R2, which has:
+ Increment: 4 (/30 = 1111 1111.1111 1111.1111 1111.1111 1
100)
+ Network address: 192.1.1.4
+ Broadcast address: 192.1.1.7
The ip 192.1.1.5 has been used by s0 of R2 so the only suitable ip address of s0 of R1 is 192.1.1.6 -> C is wrong but D is correct.
Now the last thing we must do is enabling RIP. Because e0 interface of R1 and e0 interface of R2 have the same major network (192.1.1.0/24) so we must use RIP version 2 to support discontiguous network -> F is correct.
For answer E, if we configure 2 networks
R1 (config-router)# network 192.1.1.4
R1 (config-router)# network 192.1.1.128
then these networks will be automatically summarized as 192.1.1.0 network.
Question 6
Refer to the exhibit. Two routers have just been configured by a new technician. All interfaces are up. However, the routers are not sharing their routing tables. What is the problem?
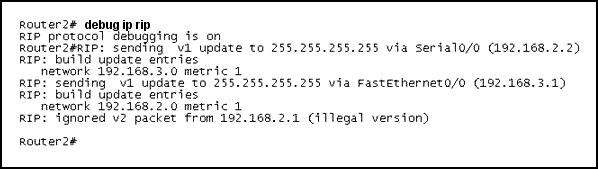
A. Split horizon is preventing Router2 from receiving routing information from Router1.
B. Router1 is configured for RIP version 2, and Router2 is configured for RIP version 1.
C. Router1 has an ACL that is blocking RIP version 2.
D. There is a physical connectivity problem between Router1 and Router2.
E. Router1 is using authentication and Router2 is not.
Answer: B
Explanation
As we can see from the output, Router2 is sending v1 update and ignoring v2 update from neighbor so we can conclude Router2 is running RIPv1. Its neighbor, Router1 (ip address of 192.168.2.1), is running RIPv2.
Notice that router running RIPv2 can “understand” RIPv1 update but router running RIPv1 cannot understand RIPv2 update
Question 7
What is the default routing update period for RIPv2?
A. 15 seconds
B. 30 Seconds
C. 180 Seconds
D. 240 Seconds
Answer: B
Question 8
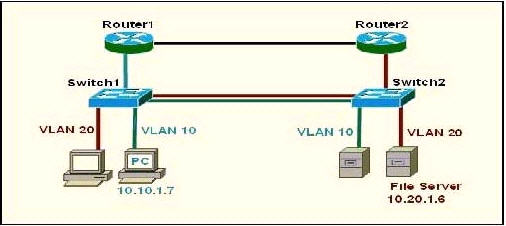
Refer to the exhibit. The network manager is evaluating the efficiency of the current network design. RIPv2 is enabled on all Layer 3 devices in the network. What network devices participate in passing traffic from the PC at 10.10.1.7 to File Server at 10.20.1.6 in the order that they will forward traffic from source to destination?
A. Switch, Switch2
B. Switch, Switch2, Router2, Switch2
C. Switch1, Router1, Switch1, Switch2
D. Switch1, Router1, Router2, Switch2
Answer: D
Explanation
The PC and File Server are in different VLANs so surely traffic from PC to File Server must go through Router1 but which path will the packet go next, through Router 2 or Switch1? Well, it is a hard question to answer.
As many comments said “the connection between R1 and Switch is Blue, so that means its under Vlan 10, and R2 to Switch 2 is red. The two routers do not have subinterfaces and are not running router on a stick basing on the color of the links” so D should be the correct answer.
Just for your information, I keep this explanation (which supports answer C) but in the exam you should choose D as your answer!
I haven’t had tested it yet but I guess that because there is a VLAN 20 on Switch 1 so Router1 will try to send that packet back to Switch1. If the link between Switch1 and Switch2 is a trunk link then the returned packet will also be sent to this link. Switch 2 receives that packet and it sends to the File Server at VLAN20. So the path will be Switch1 -> Router1 -> Switch1 -> Switch2.
There are some debates about this question but if the routers are properly configured then the packets can go from Switch1 -> Router1 -> Router2 -> Switch2 (D answer) so D can be a correct answer.
Question 9
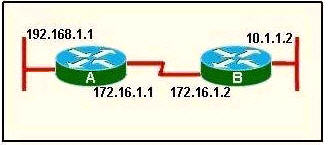
Refer to the exhibit. Router A has interfaces with addresses 192.168.1.1 and 172.16.1.1. Router B, which is connected to router A over a serial link, has interfaces with address 172.16.1.2 and 10.1.1.2.
Which sequence of commands will configure RIPv2 on router B?
A.
B( config)# router rip
B(config-router)#version 2
B(config-router)# network 172.16.0.0
B(config-router)# network 10.0.0.0
B(config-router)# end
B.
B(config)# router rip 2
B(config-router)# network 172.16.0.0
B(config-router)# network 10.0.0.0
B(config-router)# end
C.
B(config)# router rip
B(config-router)#version 2
B(config-router)# network 172.16.0.0
B(config-router)#network 192.168.1.0
B(config-router)#end
D.
B(config)# router rip version 2
B(config-router)# network 172.16.0.0
B(config-router)# network 10.0.0.0
B(config-router)#end
Answer: A
Question 10
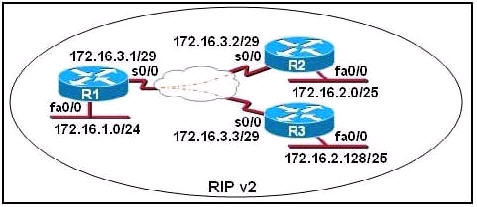
Refer to the exhibit. S0/0 on R1 is configured as a multipoint interface to communicate with R2 and R3 in this hub-and-spoke Frame Relay topology.
While testing this configuration, a technician notes that pings are successful from hosts on the 172.16.1.0/24 network to hosts on both the 172.16.2.0/25 and 172.16.2.128/25 networks. However, pings between hosts on the 172.16.2.0/25 and 172.16.2.128/25 networks are not successful. What could explain this connectivity problem?
A. The ip subnet-zero command has been issued on the R1 router.
B. The RIP v2 dynamic routing protocol cannot be used across a Frame Relay network.
C. Split horizon is preventing R2 from learning about the R3 networks and R3 from learning about the R2 networks.
D. The 172.16.2.0/25 and 172.16.2.128/25 networks are overlapping networks that can be seen by R1, but not between R2 and R3.
E. The 172.16.3.0/29 network used on the Frame Relay links is creating a discontiguous network between the R2 and R3 router subnetworks.
Answer: C
Explanation
The “ip subnet-zero” allows the use of the first subnet but it doesn’t cause this problem and we don’t have that first subnet (like 172.16.0.0/24) so we can’t confirm if the “ip subnet-zero” was used or not -> A is not correct.
Frame-Relay can use RIPv2 with no problem if we configure it correctly -> B is not correct.
In the exhibit above we notice that the s0/0 interface of R1 has not been divided into sub-interfaces so the split horizon will prevent updates from R2 to R3 and vice versa. The split horizon rule states “A router never sends information about a route back in same direction which is original information came”. In this case R2 send an update to S0/0 of R1 so R1 cannot send that update back on S0/0 -> R3 will not learn about networks of R2 (and vice versa) -> C is correct.
172.16.2.0/25 and 172.16.2.128/25 networks are not overlapping networks. They are two different sub-networks -> D is not correct.
RIPv2 is a classless routing protocol so it supports VLSM and discontiguous networks -> E is not correct.
Question 11
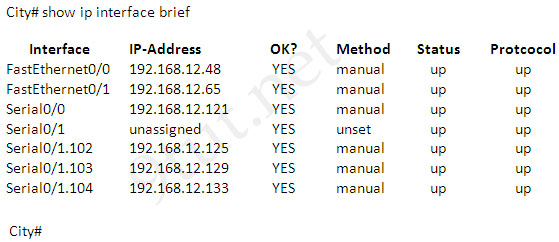
Refer to the exhibit. After a RIP route is marked invalid on Router_1, how much time will elapse before that route is removed from the routing table?
Router_1# show ip protocols
Routing Protocol is “rip”
Sending updates every 30 seconds, next due in 8 seconds
Invalid after 180 seconds, hold down 180, flushed after 240
Outgoing update filter list foe all interfaces is not set
Incoming update filter list for all interfaces is not set
Router 1# |
A. 30 seconds
B. 60 seconds
C. 90 seconds
D. 180 seconds
E. 240 seconds
Answer: B
Question 12
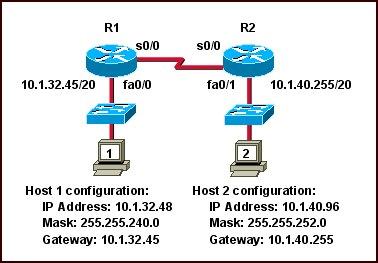
Refer to the graphic. Host 1 cannot receive packets from Host 2. Assuming that RIP v1 is the routing protocol in use, what is wrong with the IP configuration information shown? (Choose two)
A. The fa0/1 interface of router R2 has been assigned a broadcast address.
B. The fa0/1 network on router R2 overlaps with the LAN attached to R1.
C. Host 2 has been assigned the incorrect subnet mask.
D. Host 1 has been configured with the 255.255.248.0 subnet mask.
E. Host 2 on router R2 is on a different subnet than its gateway.
Answer: B C
Explanation
The fa0/1 interface of R2 is assigned an IP address of 10.1.40.255/20. It seems to be a broadcast address but it is not. If we calculate the range of this network we will understand why:
Network 10.1.40.255/20
Increment: 16 (/20 = 1111 1111.1111 1111.111
1 0000.0000 0000)
Network address: 10.1.32.0
Broadcast address: 10.1.47.255
-> 10.1.40.255/20 is an usable host address -> A is not correct.
The IP address of host 1 (10.1.32.48) belongs to the range of interface fa0/1 on R2 as shown above -> B is correct.
In the topology above, all subnet masks are /20 (255.255.240.0) excepting the subnet mask of Host 2 (255.255.252.0) so C can be incorrect.
The subnet mask of Host 1 is 255.255.240.0, not 255.255.248.0 -> D is not correct.
Host 2 is not on a different subnet than its gateway even if the subnet mask 255.255.252.0 is used. Let’s analyze the range of Host 2 network:
Network 10.1.40.96/22
Increment: 4
Network address: 10.1.40.0
Broadcast address: 10.1.43.255
Its gateway (10.1.40.255) is still belongs to this range -> E is not correct.
Note: In this question, C is the best suitable answer after eliminating A, D, E answers. But in fact Host 2 can ping its gateway because they are on the same subnet.
Question 13
What two things will a router do when running a distance vector routing protocol? (Choose two)
A. Send periodic updates regardless of topology changes.
B. Send entire routing table to all routers in the routing domain.
C. Use the shortest-path algorithm to the determine best path.
D. Update the routing table based on updates from their neighbors.
E. Maintain the topology of the entire network in its database.
Answer: A D
Question 14
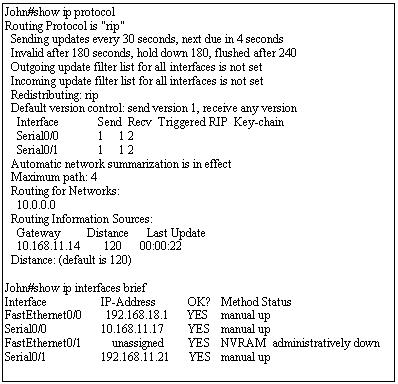
Use the output from the router shown in the graphic above to determine which of the following are correct. (Choose two)
A. Router John uses a link-state routing protocol.
B. Router John will receive routing updates on the Serial0/0 interface.
C. Router John will receive routing updates on the Serial0/1 interface.
D. Router John will send routing updates out the Serial0/0 interface.
E. Router John will send routing updates out the FastEthernet0/0 interface.
F. Router John will send routing updates out the Serial0/1 interface.
Answer: B D
Question 15
What can be determined from the line of show ip route output shown in the exhibit? (Choose two)
R 10.10.10.8 [120/2] via 10.10.10.6,00:00:25, Serial0/1
A. The next routing update can be expected in 35 seconds.
B. The IP address 10.10.10.6 is configured on S0/1.
C. The IP address 10.10.10.8 is configured on S0/1.
D. This route is using the default administrative distance.
E. The 10.10.10.8 network is two hops away from this router.
Answer: D E
Explanation
From the output, we can see 2 parameters [120/2]. The first is the administrative distance of the routing protocol being used. In this case it is RIP (symbolized by the letter “R”). Because 120 is also the default administrative distance value of RIP -> D is correct.
In RIP, the metric is hop count so “2″ means the network 10.10.10.8 is two hops (routers) away from this router.